My key takeaways
- RITA is made to detect beacons and long connections
- open source tool
- Signature based detection of malicious code is outdated
- Average detect time is over 6 month
- > 50% of compromised systems are detected by outsiders
- RITA is behaviour based
- Needs a bunch of pakets to work on
- min 1h, default 24h time frame
- high secure env: 1 week
- most commercial tools use just 20min time frames
- Requirements are minimal
- Ubuntu 18 max at the moment
- Typical setup
- Zeek to collect data
- Rita to analyse
- Rita installer will Zeek as well if not yet available
- Zeek puts logs daily into
/opt/zeek/logs/ - Mini run through as demonstrated
mkdir rita- wget install.sh for Rita
chmod +x install.shsudo ./install.sh- logout / login
- download pcap e.g from https://www.activecountermeasures.com/category/malware-of-the-day/
- translate pcap to Zeek-log by
zeek -C -r <name.pcap> - rita import
rita import *.log <name of dataset> - seems like rita is hanging, it’s OK
rita listto show databasesrita show-beacons <dataset>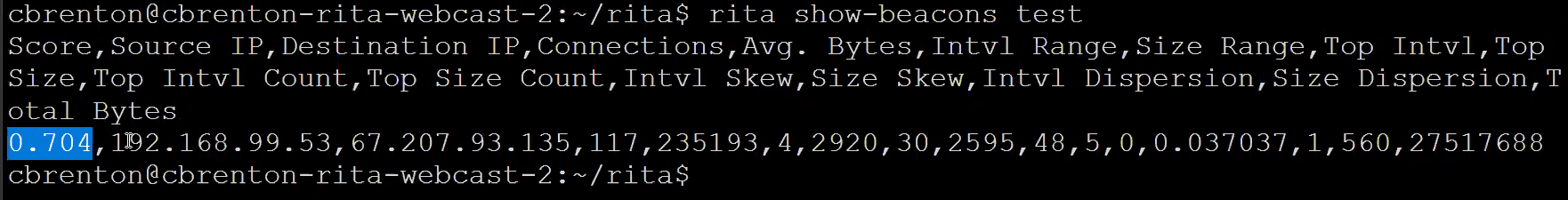
- Output
percent, source ip, dest ip, amount connection,...
- Output
- the closer the percent to 1.0, the more certain that it is a persistant connection
rita show-strobes <dataset>is to find very short and often connectionrita show-long-connections <dataset>rita show-exploded-dns <dataset>to see suspicous DNS trafficrita show-useragents <dataset>to find uncommon often connections with a certain maybe uncommon useragents
- Rita is configured by the file
/etc/rita/config.yamlrita test-config | lessto show config read only
Env
-
Provided by Active Countermeasures
-
Speaker
- Chris Brenton
- Lisa Woody
additional links

- https://www.activecountermeasures.com/free-tools/rita/
- https://github.com/activecm/rita
- https://packet-decode.s3.amazonaws.com/extra-trace2.pcap.gz
- https://www.activecountermeasures.com/blog-beacon-analysis-the-key-to-cyber-threat-hunting/
- https://www.activecountermeasures.com/threat-hunting-simplifying-the-beacon-analysis-process/
- https://www.activecountermeasures.com/alternative-dns-techniques/
- https://www.activecountermeasures.com/simulating-a-beacon/
User comments
-
Chodeng — heute um 19:37 Uhr
will limiting zeek’s capture to headers only and ignoring data in the frame (for space/operational considerations), will it impact rita’s effectiveness?wstearns-ACM — heute um 19:39 Uhr
Yes, this will affect Rita. Rita needs payload information to analyze dns traffic, User agents, etc. -
is there min zeek ‘verboseness’ requirement to effectively use rita?
- wstearns-ACM — heute um 19:40 Uhr
You need the conn, dns, http, ssl, x509, and known_certs files at a minimum.
- wstearns-ACM — heute um 19:40 Uhr
