My key takeaways
-
Humans are the de-facto top choice for cybercriminals seeking to gain access into an organization. Security Awareness & frequent simulated social engineering testing is a proven method to reduce your organization’s phish prone percentage.
-
The ideal situation for a cyber criminal or social engineer is to hijack the OODA loop by creating a knee-jerk action that effectively bypasses the first three steps and results in the attacker’s intended Action
- lures in social engineering (SE)
- Greed
- Urgency
- Curiosity
- Fear
- Self Interest
- Helpfulness
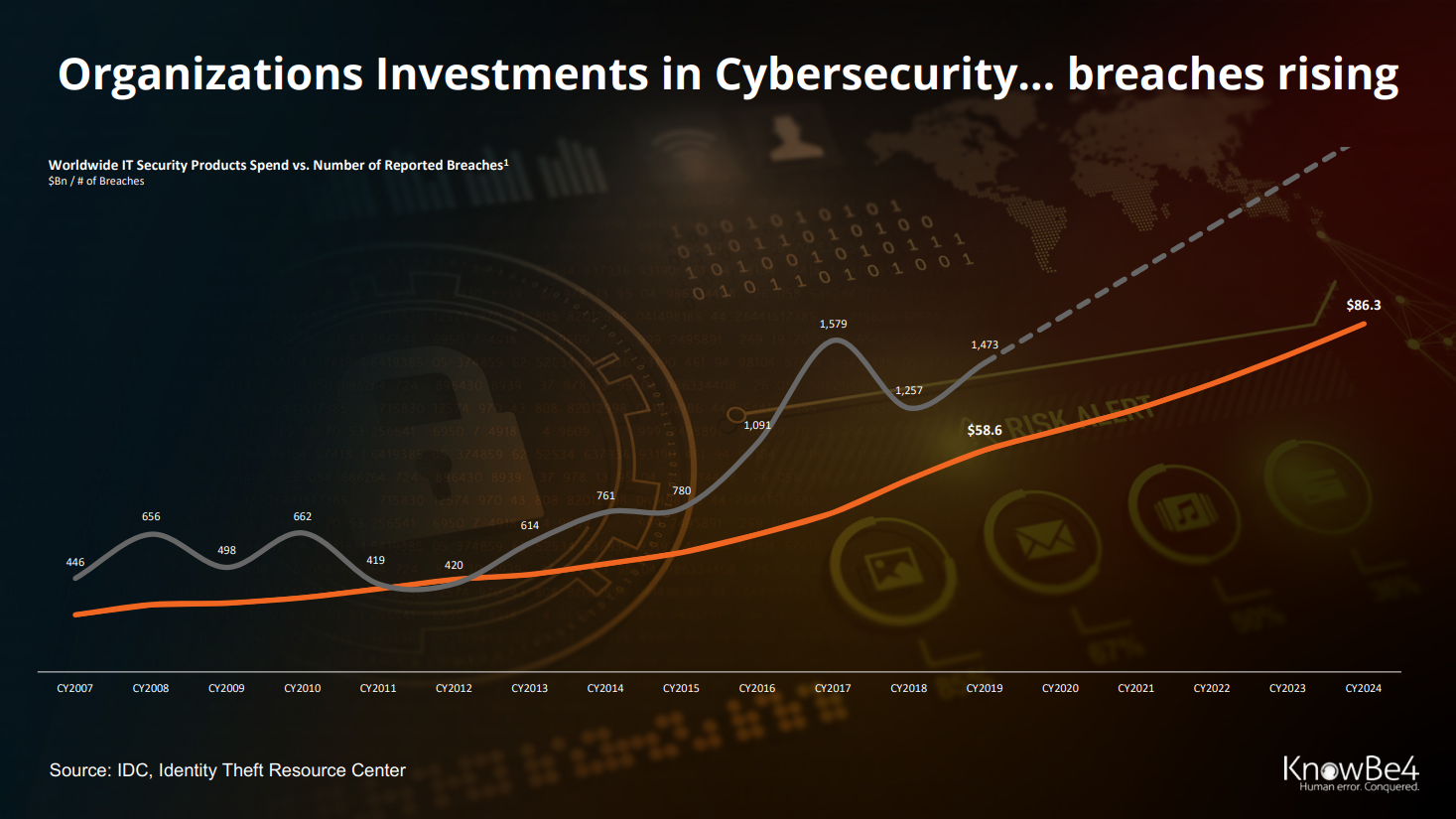
- humans are the weakest link in cybersec, but only 3% of budget is spend on them (47% in network)
- simulated social engineering attacks are recommended in NIST 800-53
- Top 5 spoofed brands
- Microsoft
- UPS
- Amazon
- Apple
- Zoom
- Why is getting the desired behaviors so difficult? 3 truths about human nature: we are lazy, social and creatures of habit (according to @bjfogg). SE will (ab)use this.
- Three Realities of Security Awareness & Culture
- Just because I’m aware doesn’t mean that I care.
- If you try to work against human nature, you will fail.
- What your employees do is way more important than what they know

- figure out where in the 10 phases of organizational security awareness you are:
- Increased awareness for infosec and IT pros
- content delivery
- platform automation
- continous testing
- security stack integration
- security orchestration
- user behaviour management (e.g. password hygiene)
- adaptive learner experience
- active user participation in security posture
- human endpoint
Env
- Provided by:
- Presenter: James R. McQuiggan
