My key takeaways
- Bad documents eg with macros enabled in SharePoint? No need to bypass phishing controls anymore!
- Documents are already trusted by users
- Difficult to trace
- M$ SmartLockout is effective to reduce direct attacks
- FireProx (AWS) or Proxycannon-ng (OpenVPN) can circumvent it
- unsolicited push notifications to bypass MFA can’t be reported as phish
- might be send esp. at beginning of the work day or after typical lunch hours
- The cloud version of the AD is available by default in Azure as Active Directory Users and Computers (ADUC)
- should be restricted by admins instantly
- Implantable file types should be checked regularly on SharePoint/OneDrive
.docm .xlsm .pptmfor Macros.proj .csprojas dev artifacts.bat .ps1 .vbaas scripts- they might be poisoned but trusted by end users!
- Macros dont try to excuted shellcode directly anymore but drop a link file in the user startup folder
- if you see spikes and anomalies on your Azure login attemps, have a closer look!
- FIDO2 might make this attack much harder
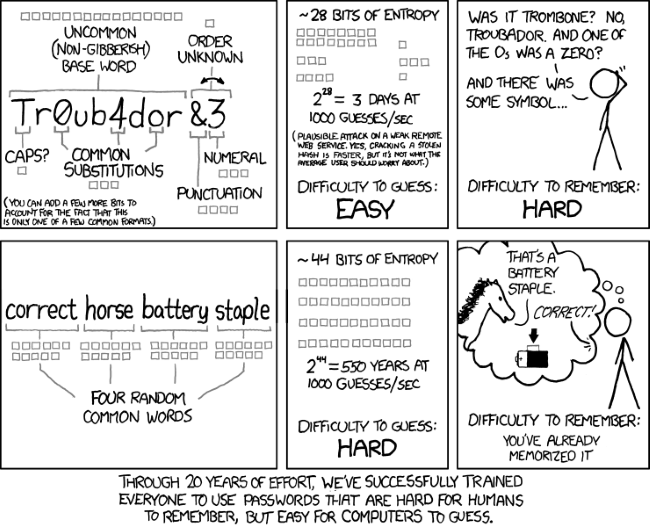
- Passwords are dead
- reduce complexity
- enforce length
Env
- Provided by BHIS
- Presenter:
additional links

- Protocol agnostic online password guessing API
- Office 365 Security: Power Automate is the New PowerShell
- creating on the fly HTTP pass-through proxies
- FIDO
- more about FIDO2
- License feature matrix for O365
User comments
- Adrian Santangelo
Protip: If you get to a push notification, try IMAP and POP. It’s enabled by default now and bypasses MFA.
- shmooz
"Just because you’re paranoid doesn’t mean they aren’t after you." ― Joseph Heller
- Ryan | The Shootist | Editor
One name you DON"T want to use for your cloud is "Sync Hole"
- nand0ps
short expiring periods leads to same password with a different number at the end
- weston
I would enforce 16 character passwords in my environment if I didn’t think it would get me fired.
