TL;DR
Diving into the essence of effective cybersecurity, this article shines a light on the transformative power of simplifying policy language, inspired by the OSI model’s structured communication layers. It goes beyond theoretical insights, offering actionable strategies for CISOs to demystify complex jargon and make cybersecurity policies accessible and engaging for every team member. Highlighting the innovative use of AI, we introduce cutting-edge methods to refine policy language, ensuring clarity, engagement, and widespread adherence. Discover how to transform cybersecurity from a document to a culture, empowering every individual within an organization to actively safeguard digital integrity.
Essentials of Effective Cybersecurity Policies for Mid-Sized Companies
In the ever-evolving landscape of cybersecurity, one critical aspect often overlooked is the language used in crafting security policies. For Chief Information Security Officers (CISOs) in mid-sized German companies, the challenge is not just about implementing cutting-edge security measures but also ensuring that these measures are comprehended and adhered to by every member of the organization. The complexity of language in security documents can unwittingly become a barrier, rendering policies ineffective no matter their technical excellence.
„A security policy is defined in a formal document that specifies what constuitutes acceptable and unacceptable behaviour of users in relation to dealing with information assets in a secure manner. It is a part of formal information security control and a baseline statement on the information security tasks which should be carried out by employees.“ (Alotaibi et al., 2016, p. 352)
This article sets out to explore the crucial role of simplicity in language, drawing parallels between the clarity required in human communication and the precision of digital protocols. Similar to how the OSI model provides a framework for data exchange across network layers, clear and straightforward language is essential for effective cybersecurity policies.
With this exploration, my goal is to provide CISOs with new methods and strategies to combat cybersecurity jargon and create security policies that are actually read. The objective extends beyond mere compliance with standards; it’s about fostering a culture of security awareness where policies are not only known but also actively practiced by every employee.
We will revisit the psychology of communication, examine how language influences security awareness, and outline practical steps to transform complex ideas into accessible, motivating directives.
Join me on this transformative journey to close the gap between the intricate world of cybersecurity and the everyday language that enables each person within an organization to actively protect digital integrity.
Simplifying Language: The First Step to Effective Cybersecurity Policies
In a digital age where cybersecurity threats loom large, clarity in communication is not just a luxury — it’s a necessity. For CISOs navigating the complex landscape of information security, the challenge often lies in ensuring that security policies are accessible and understandable to every stakeholder within an organization.
The Power of Simplicity
At its core, simplicity in language bridges the gap between complex cybersecurity concepts and their practical application. According to the ISO 24495-1 or the german DIN 8581-1 standard, which advocates for clear and simple communication in documentation, the essence of effective security policies lies in their ability to be universally understood. These standards underscore the critical role of simplicity, particularly in a field as intricate as cybersecurity, where the stakes are invariably high.
„[…] the UK information breaches survey found that 70% of organisations with a poorly understood security policy had staff-related breaches, whereas only 41 % of organisations where the policy was well understood had any of these.“ (Alotaibi et al., 2016, p. 352)
The Barrier of Complexity
Complexity in language not only alienates non-technical staff but also obscures the critical nature of cybersecurity practices. A study by the University of Hamburg highlighted a concerning figure: approximately 12.1% of German-speaking adults between the ages of 18 and 64 face significant challenges in literacy, directly impacting their ability to comprehend complex documents (LEO-Study, University of Hamburg, 2018). This statistic is a strong reminder of the need for simplicity in security policy documentation to ensure inclusivity and comprehensibility.
Bridging the Gap
The analogy of the OSI model in networking provides a useful parallel. Just as this model outlines clear layers for data transmission, simplifying the language in security policies establishes clear, understandable guidelines for every user. By adopting simpler language, CISOs can make cybersecurity policies more than just documents; they can transform them into actionable, lived practices across the organization.
The Psychological Aspect
From a psychological perspective, simplicity in language not only enhances comprehension but also engagement. When individuals understand the "why" and "how" of security policies, they are more likely to internalize these practices, leading to a stronger security culture. This psychological engagement is crucial in fostering a proactive stance towards cybersecurity, moving beyond mere compliance to genuine, informed participation.
In today’s work environment, characterized often by high stress, the complexity of language in security policies can add an additional layer of strain. Under stress, neurological processing capabilities significantly diminish, limiting rational thinking. Simplified language is thus not only crucial for inclusion of individuals with learning disabilities but also acts as an effective tool for stress reduction. When employees are under pressure, clear and straightforward language in security policies enables quick and direct comprehension. This approach helps to alleviate feelings of being overwhelmed and promotes a more effective implementation of security measures, ensuring that policies are not merely read but understood and applied.
In Conclusion
Simplicity in cybersecurity documentation is not about dumbing down critical information; it’s about elevating understanding and action across all levels of an organization. As we delve deeper into the digital era, the clarity of our communication will undoubtedly play a pivotal role in our collective security posture. For CISOs, the task ahead is clear: to demystify the complexities of cybersecurity, making it accessible and actionable for every member of their team.
Incorporating the concept of encapsulation and data transformation across OSI model layers further enriches the analogy between technical communication in network systems and the clarity needed in cybersecurity policies.
Applying OSI Model Principles for Clearer Cybersecurity Policies
In the realm of cybersecurity, communication stands as the linchpin between sophisticated technical defenses and their real-world application. This intricate dance of conveying complex protocols into actionable, everyday practices can be likened to the OSI model, a foundational framework in the world of network communication. The OSI model, with its seven-layered approach to data transmission, offers a compelling analogy for understanding how security policies transition from high-level concepts to tangible actions.
At the apex of the OSI model sits the Application Layer (Layer 7), which serves as a perfect metaphor for the comprehensive security policies that organizations strive to implement today. These policies, much like the applications operating at Layer 7, are designed to be the ultimate interface with the user, translating the organization’s security framework into terms and directives that are accessible and relevant. However, for these policies to be effective, they must be understood and acted upon by every individual within the organization, necessitating clarity and simplicity in their formulation.
Descending to the foundational level, the Physical Layer (Layer 1) of the OSI model symbolizes the concrete enactment of security measures and cyber hygiene practices prescribed by these policies. It’s here that the abstract principles of cybersecurity are grounded into physical reality, through the adherence to best practices, the use of secure passwords, and the maintenance of up-to-date antivirus software, among others. Each layer in between, from Data Link to Presentation, can be seen as steps in the decapsulation process, removing layers of specificity and guidance to translate high-level policies into actionable steps.
However, the complexity of language in policy documentation often acts as a barrier to this translation process. The more technical and jargon-laden the language, the more challenging it becomes for the intended audience to grasp and implement the outlined security measures. It’s essential, therefore, for cybersecurity policies to be articulated in a manner that is as clear and straightforward as the data encapsulation process within the OSI model. By simplifying the language used in these documents, organizations can ensure that the essence of their security protocols is not lost in translation.
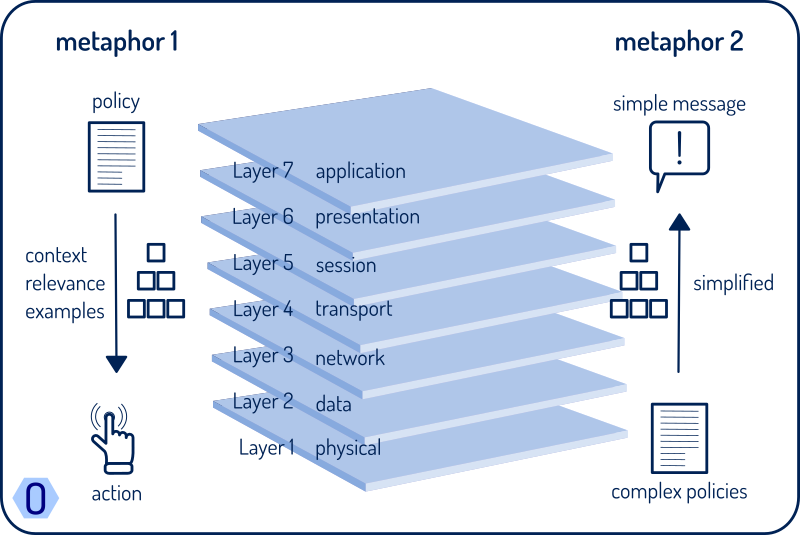
Ultimately, the goal of any cybersecurity policy is to protect what could be considered the ‘eighth layer’ in the OSI analogy — the human element. Recognizing that individuals are the ultimate enforcers of any security policy, it’s critical that these documents are crafted with the end-user in mind, enriched at each "layer" with context and guidance relevant to their daily operations. In reversing the analogy, one could envision the policy itself as the foundation (Layer 1), progressively enriched with details and context through the layers, ensuring that by the time it reaches the human element, it’s not just understood but integrated into everyday actions.
By drawing on the OSI model as a metaphor for effective communication in cybersecurity, we underscore the importance of clear, accessible language in bridging the gap between technical defenses and human actors.
Evidence-Based Strategies for Crafting Effective Cybersecurity Policies
And the impact of language complexity on cybersecurity compliance and risk management cannot be overstated. Studies and real-world examples underscore the pivotal role of simplifying security policies to enhance organizational compliance and security posture. This section delves into the evidence supporting this approach and highlights best practices from various sectors.
Several studies have investigated the impact of simplification on compliance, across different fields, revealing how simplifying processes, information, or regulations can significantly affect adherence and outcomes, e.g. De Neve et al. (2019) explored the effects of simplification, deterrence, and tax morale on tax compliance through population-wide experiments in Belgium. They found that simplifying communication significantly increases compliance, more so than deterrence messages or invoking tax morale. This study suggests that simplification can be far more cost-effective than standard enforcement measures, potentially leading to substantial savings on enforcement costs (De Neve et al., 2019).
The thesis that complex language and issues in understanding security policies by users can lead to security risks is supported by various studies. Here are some key findings from the literature:
-
Non-compliance with information security policy is a major challenge, often attributed to human factors rather than technical issues. Simplifying policies and enhancing user understanding can mitigate risks associated with policy non-compliance (M. Alotaibi, S. Furnell, & N. Clarke, 2016).
-
The complexity of cybersecurity risk management can be addressed through game theory approaches, suggesting that simplification and strategic communication of security policies can enhance organizational security (D. Akinwumi, G. Iwasokun, B. K. Alese, & S. Oluwadare, 2018).
-
User behavior plays a crucial role in cybersecurity management. Studies on psychological traits and individual differences among users suggest that clearer and more understandable security policies could significantly improve cybersecurity by mitigating the impact of social engineering and cognitive hacking (A. Moustafa, Abubakar Bello, & A. Maurushat, 2021).
These studies collectively underline the importance of developing security policies that are easy to understand and follow, suggesting that complexity in policy language not only hampers user comprehension but also leads to increased security risks.
The academic literature also suggests several approaches for simplifying the language in security policies, aiming to make them more understandable and accessible to users. Here are some examples and suggestions:
-
Standard Security Policy Language (SSPL): SSPL is designed to allow security officers to develop their own security policies in a readable, formal format. This language simplifies the task of developing standard, unambiguous policy statements, making it easier for non-experts to understand and comply with security policies (M. Al-Morsy & H. Faheem, 2009). Unfortunatly even 15 years later, this language didn’t become a widely accapted standard.
-
Survey on Policy Languages in Network and Security Management: This study discusses the evolution of policy-driven systems and the significance of policy languages in expressing the intentions of administrators, particularly focusing on network and security management. The discussion includes key issues and future work of policy languages, providing insights into how language design can contribute to simplifying policy expressions (Weili Han & Chang Lei, 2012).
-
Formal Security Policy Implementations in Network Firewalls: Discusses the transition from high-level, natural language policies created by management to device-specific policies written by administrators. This paper highlights the need for a clear and coherent methodology for creating, managing, and deploying security policies, suggesting that a more structured approach to policy language can simplify these tasks (Macfarlane et al., 2012).
These studies underscore the importance of using clear, structured, and standard languages for security policies to improve their accessibility and effectiveness in ensuring security compliance.
The evidence is clear: simplifying the language of cybersecurity policies not only enhances compliance but also fortifies an organization’s defense against cyber threats.
By embracing best practices from within and outside the cybersecurity realm, organizations can ensure that their policies are not just written but understood and acted upon. This approach not only mitigates risk but also fosters a culture of security awareness and responsibility across all levels of the organization.
Best Practices to Ensure Your Cybersecurity Policy is Effective and Inclusive
 |
1. Use Plain Language: Avoid jargon and technical terms that may not be universally understood. If technical terms must be used, provide clear definitions. |
 |
2. Visual Aids: Incorporate diagrams, flowcharts, and infographics to illustrate complex processes and guidelines. |
 |
3. Segmentation: Break down policies into sections or bullet points, focusing on one key action or idea per segment to facilitate understanding and recall. |
 |
4. Feedback Loops: Encourage feedback on the clarity of security policies and use this input to make continuous improvements. |
 |
5. Regular Training: Complement simplified policies with regular, engaging training sessions to reinforce key concepts and procedures. |
Example for a simplification
Let’s apply the theory you’ve read so far. We’ll use a SANS Acceptable Use Policy (AUP) template (SANS, 2022) for a fictional company, ACME Inc., chosen for its public availability and lack of copyright restrictions. This choice is by no means a critique of SANS’s content!
To simplify the Acceptable Use Policy (AUP) for ACME Inc., the strategy focuses on reducing complexity, removing jargon, and breaking down concepts into more digestible, straightforward language. This approach ensures that all employees, regardless of their position or familiarity with technical terms, can understand and adhere to the policy.
Let’s illustrate this with examples from the original text and their simplified versions:
1. Example: Overview Section
Original
"Infosec Team’s intentions for publishing an Acceptable Use Policy are not to impose restrictions that are contrary to ACME Inc.’s established culture of openness, trust and integrity. ACME Inc. is committed to protecting ACME Inc.’s employees, partners and the company from illegal or damaging actions by individuals, either knowingly or unknowingly."
Simplified
"At ACME Inc., we value openness, trust, and integrity. This policy helps us keep ACME and everyone involved safe from harm online. It’s about using our internet, computers, and other tech tools responsibly and safely."
Explanation: The original paragraph focuses on the intentions behind the AUP, emphasizing the balance between freedom and security. The simplified version retains this essence but communicates it in everyday language. It directly addresses the reader ("At ACME Inc."), makes the purpose of the policy clear, and uses accessible terms like "keep safe from harm online" and "using our tech tools responsibly."
2. Example: Purpose Section
Original
"The purpose of this policy is to outline the acceptable use of computer equipment and other electronic devices at ACME Inc. These rules are in place to protect the employee and ACME Inc. Inappropriate use exposes ACME Inc. to cyber risks including virus attacks including ransomware, compromise of network systems and services, data breach, and legal issues."
Simplified
"Our tech tools and systems are here to help us work better. It’s important that we use them in a way that’s good for everyone, keeps our data safe, and follows the rules."
Explanation: The simplified version distills the purpose of the policy to its core: using technology in a beneficial, safe, and rule-abiding manner. It avoids technical terms like "cyber risks," "ransomware," and "data breach," which might be confusing for some readers, instead opting for general language that still conveys the importance of security.
3. Example: General Use and Ownership (4.1.1)
Original
"ACME Inc. proprietary information stored on electronic and computing devices whether owned or leased by ACME Inc., the employee or a third party, remains the sole property of ACME Inc.. You must ensure through legal or technical means that proprietary information is protected in accordance with the Data Protection Standard."
Simplified
"Protecting ACME’s Secrets: Anything you work on or with at ACME belongs to the company. Keep it safe and don’t share it without permission."
Explanation: This simplification reduces the formal and technical nature of the original statement to a clear, action-oriented guideline. "Proprietary information" becomes "ACME’s secrets," a term easier for everyone to grasp. The instruction is made more direct: "Keep it safe and don’t share it without permission," emphasizing personal responsibility in a straightforward manner.
4. Example: Unacceptable Use (4.3.1)
Original
"Under no circumstances is an employee of ACME Inc. authorized to engage in any activity that is illegal under local, state, federal or international law while utilizing ACME Inc.-owned resources."
Simplified
"Don’t use ACME tech for illegal stuff."
Explanation: This simplification gets straight to the point, removing the detailed legal references to focus on the core directive: avoid illegal activities with company resources. It transforms a formally structured sentence into a simple rule, making it instantly understandable.
Balancing Simplicity and Precision in Cybersecurity Policies
Using simplified language in official company policies aims to make them more accessible and understandable to a broader audience, promoting inclusivity and ensuring that all employees have a clear understanding of their obligations and rights. However, there are several drawbacks to this approach:
1. Loss of Precision
Legal and technical documents often use specific terminology to convey precise meanings. Simplified language might lack the necessary precision, leading to ambiguity. This can result in misunderstandings about policy requirements or the scope of policy provisions.
2. Undermining Legal Strength
The legal enforceability of a policy may be compromised if simplified language fails to capture the necessary legal nuances. This could pose challenges in situations where the company needs to enforce the policy or defend its actions based on the document.
3. Over-simplification
There’s a risk of oversimplifying complex concepts, which can lead to a lack of depth in understanding among employees. This might result in employees not fully grasping the importance or implications of certain policies, reducing their effectiveness.
4. Limited Audience Consideration
While simplified language aims to be more inclusive, it may not meet the needs of all audience segments. For instance, individuals with advanced knowledge or those looking for detailed information might find simplified policies lacking in depth and specificity.
5. Potential for Increased Queries
A simplified policy might lead to an increase in queries to the legal or HR departments because employees may seek clarification on points they perceive as too vague or broadly defined. This could place a strain on resources and reduce efficiency.
6. Risk of Overgeneralization
Simplified language might lead to the overgeneralization of policies, which can be problematic in situations that require tailored, specific guidance. This could result in policies that are too broad to be effectively applied in certain scenarios.
7. Challenges in Translation
For multinational companies, policies need to be translated into multiple languages. Simplified English does not always translate cleanly into other languages, which could lead to inconsistencies in the interpretation of policies across different regions.
A Strategic Approach to Developing Actionable Cybersecurity Policies
While the use of simplified language in official company policies has notable benefits, particularly in terms of accessibility and inclusivity, it’s important to balance simplicity with precision, legal robustness, and comprehensiveness. Crafting policies that are both accessible and precise often requires careful consideration, expert input, and possibly a layered approach—providing simplified summaries accompanied by detailed, legally rigorous documents.
Adopting a multi-staged approach to policy documentation can effectively address this challenge. This strategy involves creating two versions of each policy: a simplified version for broad accessibility and understanding, and a formal, legally comprehensive version that remains the binding document. All while having limited ressources!
The Role of AI in Simplifying Policies
The rise of AI technologies offers significant opportunities to streamline the process of simplifying complex policy documents. AI can analyze detailed legal and technical texts, extracting key points and translating them into plain language. This reduces the workload on human resources, ensuring consistency across documents and potentially offering insights into areas that frequently require clarification. AI can also assist in maintaining the alignment between simplified and formal versions, ensuring that simplifications do not introduce discrepancies with the legally binding text.
Actionable Tips and Prompts for Using AI in Policy Simplification
1. Initial Analysis and Extraction:
- Use AI to analyze the formal policy document and identify key concepts, obligations, rights, and prohibitions.
- Example prompt: "Identify and summarize the core principles and obligations outlined in this policy document."
2. Drafting Simplified Content:
- Instruct AI to draft simplified explanations of identified concepts, using plain language and avoiding jargon.
- Example prompt: "Translate these legal terms and concepts into plain language suitable for a general audience."
3. Ensuring Consistency:
- Utilize AI to compare the simplified version against the original, highlighting any areas where the simplification may have altered the meaning or left out crucial details.
- Example prompt: "Compare the simplified text to the original policy document and identify any discrepancies or omitted essential details."
4. Iterative Improvement:
- Implement feedback loops where the AI-generated simplifications are reviewed by legal and subject matter experts, and refine the AI model based on their corrections and suggestions.
- Example prompt: "Refine the simplified document based on this expert feedback focusing on accuracy, completeness, and clarity: [feedback]"
5. Accessibility and Engagement:
- Employ AI to suggest visual aids or other engagement tools that can complement the simplified text, making the policies not just easier to read but also to understand.
- Example prompt: "Generate suggestions for visual aids or interactive elements that can enhance understanding of these policy points."
Advantages of a Multi-Staged Approach
This approach ensures that policies are accessible to all employees, regardless of their legal or technical knowledge, while maintaining the integrity and enforceability of the company’s policies. The simplified version serves as an entry point, fostering greater engagement and understanding among employees. Meanwhile, the formal version provides the legal foundation and detailed guidance necessary for implementation and compliance.
By leveraging AI in this multi-staged approach, companies can efficiently produce high-quality, accessible policy documentation. This not only enhances compliance and understanding but also demonstrates a commitment to inclusivity and transparency. Moreover, AI-driven simplification can adapt over time, learning from feedback and evolving with changes in policy or law, ensuring that both versions of the policy remain aligned and current.
Crafting Effective Cybersecurity Policies: Lessons from the OSI Model
In wrapping up our exploration into crafting effective cybersecurity policies, it becomes evident that the essence of these policies parallels the OSI model’s approach to network communication—layered, structured, and universally comprehensible. Just as the OSI model facilitates seamless data exchange through clarity and order across its layers, an effective cybersecurity policy is built on the foundation of clear language and structured guidance that speaks to every member of the organization. This analogy not only underscores the importance of simplicity and accessibility in policy documentation but also highlights the strategic layering of information, ensuring that each stakeholder engages with the policy at the level of their understanding and responsibility. Therefore, as we draw from the technical wisdom of the OSI model, let’s commit to developing cybersecurity policies that are not just technically robust but also inclusive and empowering, ensuring that every layer of our organizations stands united and resilient in the face of cyber threats.
Share your experiences with implementing this approach in your company! Feel free to leave a comment below or reach out directly via email. Your insights are invaluable.
Sources
-
Acceptable Use Policy. (2022). SANS™ Institute. https://www.sans.org/information-security-policy/
-
Akinwumi, D. A., Iwasokun, G. B., Alese, B. K., & Oluwadare, S. A. (2018). A review of game theory approach to cyber security risk management. Nigerian Journal of Technology, 36(4), 1271. https://doi.org/10.4314/njt.v36i4.38
-
Al-Morsy, M., & Faheem, H. (2009). A new standard security policy language. IEEE Potentials, 28(2), 19–26. https://doi.org/10.1109/MPOT.2008.931574
-
Alotaibi, M., Furnell, S., & Clarke, N. (2016). Information security policies: A review of challenges and influencing factors. 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), 352–358. https://doi.org/10.1109/ICITST.2016.7856729
-
De Neve, J.-E., Imbert, C., Spinnewijn, J., Tsankova, T., & Luts, M. (2021). How to Improve Tax Compliance? Evidence from Population-Wide Experiments in Belgium. Journal of Political Economy, 129(5), 1425–1463. https://doi.org/10.1086/713096
-
Grotlüschen, A., Buddeberg, K., & Solga, H. (Hrsg.). (2023). Interdisziplinäre Analysen zur LEO Studie 2018 – Leben mit geringer Literalität: Vertiefende Erkenntnisse zur Rolle des Lesens und Schreibens im Erwachsenenalter. Springer VS.
-
Han, W., & Lei, C. (2012). A survey on policy languages in network and security management. Computer Networks, 56(1), 477–489. https://doi.org/10.1016/j.comnet.2011.09.014
-
Macfarlane, R., Buchanan, W., Ekonomou, E., Uthmani, O., Fan, L., & Lo, O. (2012). Formal security policy implementations in network firewalls. Computers & Security, 31(2), 253–270. https://doi.org/10.1016/j.cose.2011.10.003
-
Moustafa, A. A., Bello, A., & Maurushat, A. (2021). The Role of User Behaviour in Improving Cyber Security Management. Frontiers in Psychology, 12, 561011. https://doi.org/10.3389/fpsyg.2021.561011
